Dear followers,
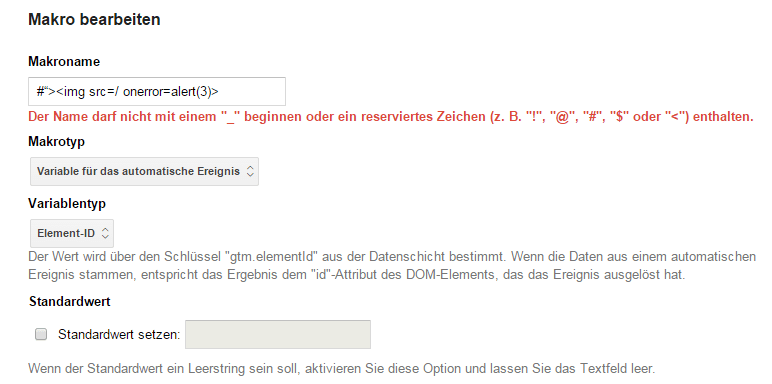
i recently searched for vulnerabilities on a Google service called tagmanager, this service is used for SEO operations. My main research was to look for any field that could be vulnerable to Cross Site Scripting, but every field was protected against special characters as you can see in the image below. So pretty useless to search on further on this.
So the next thing i saw was that the Tagmanager allowed a user to upload a set of definitions, tags, and Macros in form of a JSON File. 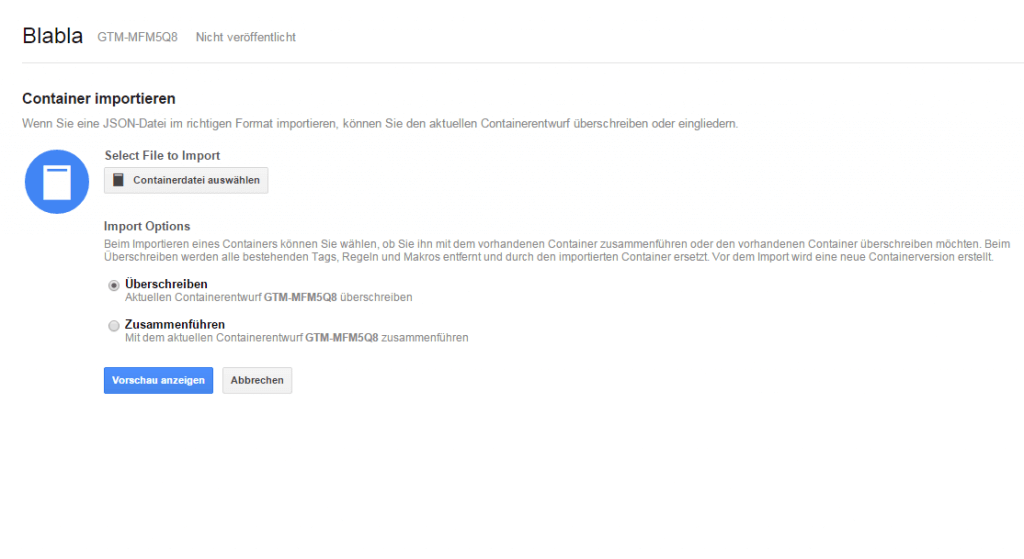
What i did next was to download the sample JSON file and edited the Name fields of the macros (which were not allowed special characters)
"data": {
"name": "#“><img src="/" onerror="alert(3)">",
"type": "AUTO_EVENT_VAR",
"autoEventVarMacro": {
"varType": "HISTORY_NEW_URL_FRAGMENT"
}
And guess what ? After uploading and overwriting the settings, the Payload got executed.
Here’s the POC Video i sent in
Hope you enjoyed! 🙂
all the best
Patrik