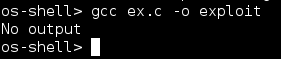From nobody to Root Advanced SQL-Injection
Dear readers, today i’m going to write about a SQLInjection which led to full control over a Server:
The target was a login form with a SQL-Injection in the Parameter Password. With guessing the Username “Admin” and the Password ‘
The well known SQL error came up
From this point i knew that there is potential on this server ;-). The next step was to point SQLmap (a SQL-Injection Takeover tool) to the IP-Address 192.168.179.2/login.hmtl and add the attributes –forms to tell SQLmap to look for possible injectable parameters in the Form Parameters (Username & Password)
Bujaka! Sqlmap found the injectable Parameters and is now ready to exploit the Database. Apart from only dumping the database we can also use the option –os-shell which will give us a command prompt on the target system. But not only a prompt SQLmap offers us a form to upload files on the target system we could upload some malicious files php shells, but i wanted to go further.
The first step as i gained a shell was to view which privileges do i have on the system. The output was a bit disapointing… i am the user “nobody” and yeah i can do … nothing as a nobody… okay not very much ;-). The next thing i’ve done was to check out the Kernel Version of the underlying System. I am on a Ubuntu i686 (32Bit) System with Kernel Version 2.6.32.-21-generic.
After digging arround in the depths of the internet i found that there was an Local Root Exploit for this Kernel Version
A ‘local exploit’ requires prior access to the vulnerable system and usually increases the privileges of the person running the exploit past those granted by the system administrator.
This is exactly what i planted to do: To inrease my privilege level on this machine. So i copied the exploit code compiled it with a system shell.
After compiling with no error i tried to run it.
Yay! I am root!