tldr;
A Private Bug Bounty Program had a globally readable .htpasswd file. I cracked the DES hash, got access to development and staging environments and was rewarded a shitload of$.
[Tools used]
dirbuster https://www.owasp.org/index.php/Category:OWASP_DirBuster_Project
John http://www.openwall.com/john/
[\Tools used]
Today I want to share something with you that I recently discovered in a private Bug Bounty Program. Due to private program restrictions, I am not allowed to disclose the identifying details of the bug, so I’m just going to share my techniques and how I discovered it.
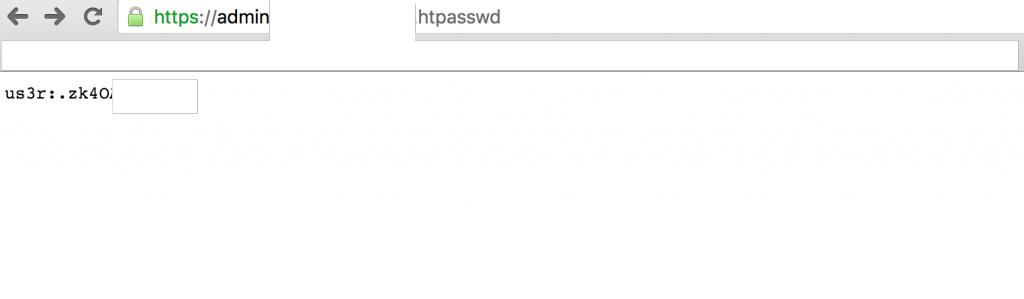
So, as a first step, I looked for potential vulnerable subdomains using a Google Dork query: site:*.REDACTED.com -www and then looked for interesting stuff. One particular domain caught my attention and so I had a look at it, admin.REDACTED.com. Upon review, the site looked pretty unspectacular and so I decided to use the tool „dirbuster“ to look for the juicy stuff. I was about to give up when I saw the tool discovered a .htpasswd file with an HTTP status 200. With a bit of excitement, I visited the URL and was pretty surprised to the file rendered.
So what exactly is this? As some of you may know, several webservers offer a mechanism called Basic Authentication. While I now knew the username was us3r, the password was still encrypted… Now, in similar cases, I’ve seen passwords simply being Base64 encoded but here, the encryption didn’t look like anything I was familiar with. After some Googling, I realized it was DES (Data Encryption Standard).. Based on what I read, while DES is now considered insecure and susceptible to theoretical attacks (thanks Wikipedia), there are no trivial methods known for DES cracking. So instead, I used a simple password cracking tool called john with the help of @nijagaw Nico who pointed me to a nice wordlist (Link) to crack it.
Loaded 1 password hash (descrypt, traditional crypt(3) [DES 128/128 SSE2-16])
After some time i finally had the encrypted password.
john --wordlist=/Users/Patrik/Downloads/crackstation.txt pw Loaded 1 password hash (descrypt, traditional crypt(3) [DES 128/128 SSE2-16]) Press 'q' or Ctrl-C to abort, almost any other key for status 0g 0:00:00:04 5% 0g/s 3316Kp/s 3316Kc/s 3316KC/s 09554858..09554972 0g 0:00:00:27 52% 0g/s 2953Kp/s 2953Kc/s 2953KC/s 42333281..42333395 0g 0:00:00:28 54% 0g/s 2971Kp/s 2971Kc/s 2971KC/s 45154098..45154206 0g 0:00:01:56 35% 0g/s 3055Kp/s 3055Kc/s 3055KC/s CFCbu..CF(CC sasi21033****** (?) Use the "--show" option to display all of the cracked passwords reliably Session completed
But what now? The website itself didn’t use any kind of .htaccess and, admittedly, I was a bit lost. However, thanks to the awesome @mongobug, I was able to figure out that each of the following was using Basic Authentication:
- thestageingstuff.*.domain.com
- developmentworkshere.*.domain.com
- quark.*.domain.com
- devsfavourite.*.domain.com
Additionally, the fun thing was the Username and Password I discovered worked on each and every one of them. In other words,I had access to the company’s development / beta environments.
The next step? Report it to the program owner who responded quickly, and resolved the issue even quicker. Kudos to them.
End of the story 🙂